Microsoft
Microsoft is having another whack at its controversial Recall feature for Copilot+ Windows PCs, after the original version crashed and burned amid scrutiny from security researchers and testers over the summer. The former version of Recall recorded screenshots and OCR text of all user activity, and stored it unencrypted on disk where it could easily be accessed by another user on the PC or an attacker with remote access.
The feature was announced in late May, without having gone through any of the public Windows Insider testing that most new Windows features get, and was scheduled to ship on new PCs by June 18; by June 13, the company had delayed it indefinitely to rearchitect it and said that it would be tested through the normal channels before it was rolled out to the public.
Today, Microsoft shared more extensive details on exactly how the security of Recall has been re-architected in a post by Microsoft VP of Enterprise and OS Security David Weston.
More secure, also optional
Microsoft
The broad strokes of today’s announcement are similar to the changes Microsoft originally announced for Recall over the summer: that the feature would be opt-in and off-by-default instead of opt-out, that users would need to re-authenticate with Windows Hello before accessing any Recall data, and that locally stored Recall data will be protected with additional encryption.
However, some details show how Microsoft is attempting to placate skeptical users. For instance, Recall can now be removed entirely from a system using the “optional features” settings in Windows (when a similar removal mechanism showed up in a Windows preview earlier this month, Microsoft claimed it was a “bug,” but apparently not).
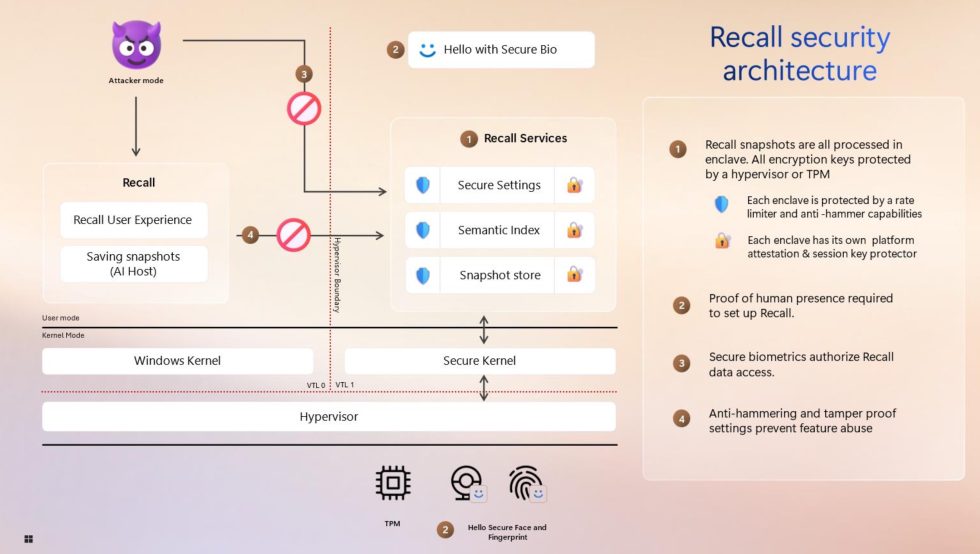
The company is also sharing more about how Windows will protect data locally. All Recall data stored locally, including “snapshots and any associated information in the vector database,” will be encrypted at rest with keys stored in your system’s TPM; according to the blog post, Recall will only function when BitLocker or Device Encryption is fully enabled. Recall will also require Virtualization-Based Security (VBS) and Hypervisor-Protected Code Integrity (HVCI) enabled; these are features that people sometimes turn off to improve game performance, but Recall will reportedly refuse to work unless they’re turned on.
This is because the new Recall operates inside of a VBS enclave, which helps to isolate and secure data in memory from the rest of the system.
“This area acts like a locked box that can only be accessed after permission is granted by the user through Windows Hello,” writes Weston. “VBS enclaves offer an isolation boundary from both kernel and administrative users.”
Windows doesn’t allow any code to run within these enclaves that hasn’t been signed by Microsoft, which should lower the risk of exposing Recall data to malware or other rogue applications. Other malware protections new to this version of Recall include “rate-limiting and anti-hammering measures.”
